
Hackers Modifying Registry Keys to Establish Persistence via Scheduled Tasks
Persistence is one of the key things for threat actors to maintain their access to compromised systems and establish connections whenever they require. One of the key methods used to maintain persistence is the use of scheduled tasks.
A threat actor who is identified as “HAFNIUM” has been discovered to be using an unconventional method to tamper with scheduled tasks for establishing persistent connections by modifying the registry keys in their Tarrask malware. This enables the threat actor to create stealthy scheduled tasks
Hackers Modifying Registry Keys
According to the reports shared by the Purple team, a proof of concept called GhostTask has been published, which exploits the scheduled tasks via a beacon object file that can enable red teamers and threat actors to use it within a C2 framework.
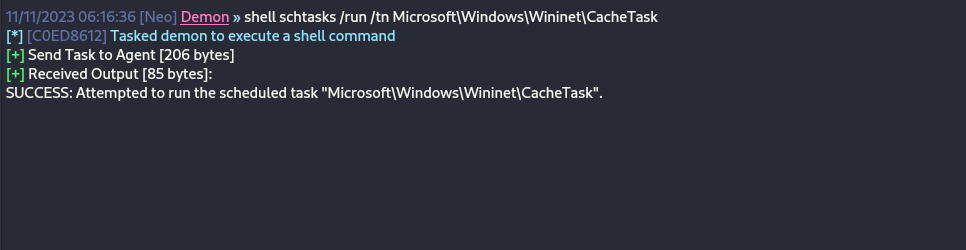
The scheduled task tampering technique is re-created by creating the associated registry keys that prevalently required elevated privileges. GhostTask requires a scheduled task that already exists in the target system.
Once the registry keys are modified, the system requires a restart for changes to take effect. Still alternatively, the schtasks utility can be used to initiate the task and establish persistence.
Windows Events
This technique relies on modifying the registry keys; hence, registry events enabled from the Group Policy must be audited. Additionally, the TaskCache registry key containing new or modified scheduled tasks must be monitored for any changes.
Auditing the registry keys provides log visibility whenever a registry key is accessed or modified that is captured under the event IDs 4657 (Registry Value Modification) and 4663 (Registry Object Access).
Registry
Scheduled tasks created by manipulating the registry keys do not appear in the Task Scheduler or the schtasks /query command. Though it can be hidden by the deletion of the SD registry key, it requires SYSTEM-level privileges that can result in detection opportunities in terms of privilege escalation.
Furthermore, a complete report about this scheduled task tampering has been published, which provides detailed information about the report from Microsoft, attack methods, techniques, exploitation, and other information.
Source: https://bit.ly/42Wk1gd



