
WARNING: Hackers’ New Favorite Tool – Weaponized SVG Files!
Threat actors use SVG files in cyber-attacks because SVGs (Scalable Vector Graphic files) can contain embedded scripts, making them a vector for executing malicious code.
Not only that even the SVG files can also bypass certain security measures as well due to their ability to blend in with legitimate web content.
Recently, cybersecurity researchers at Cofense discovered that hackers are increasingly using weaponized SVG files in cyber attacks.
Weaponized SVG Files
SVG files are advanced vectors for evolving malware delivery, which surged with AutoSmuggle in May 2022, facilitating the malicious payloads in HTML/SVG.
Besides this, threat actors have exploited it in two major campaigns since December 2023.
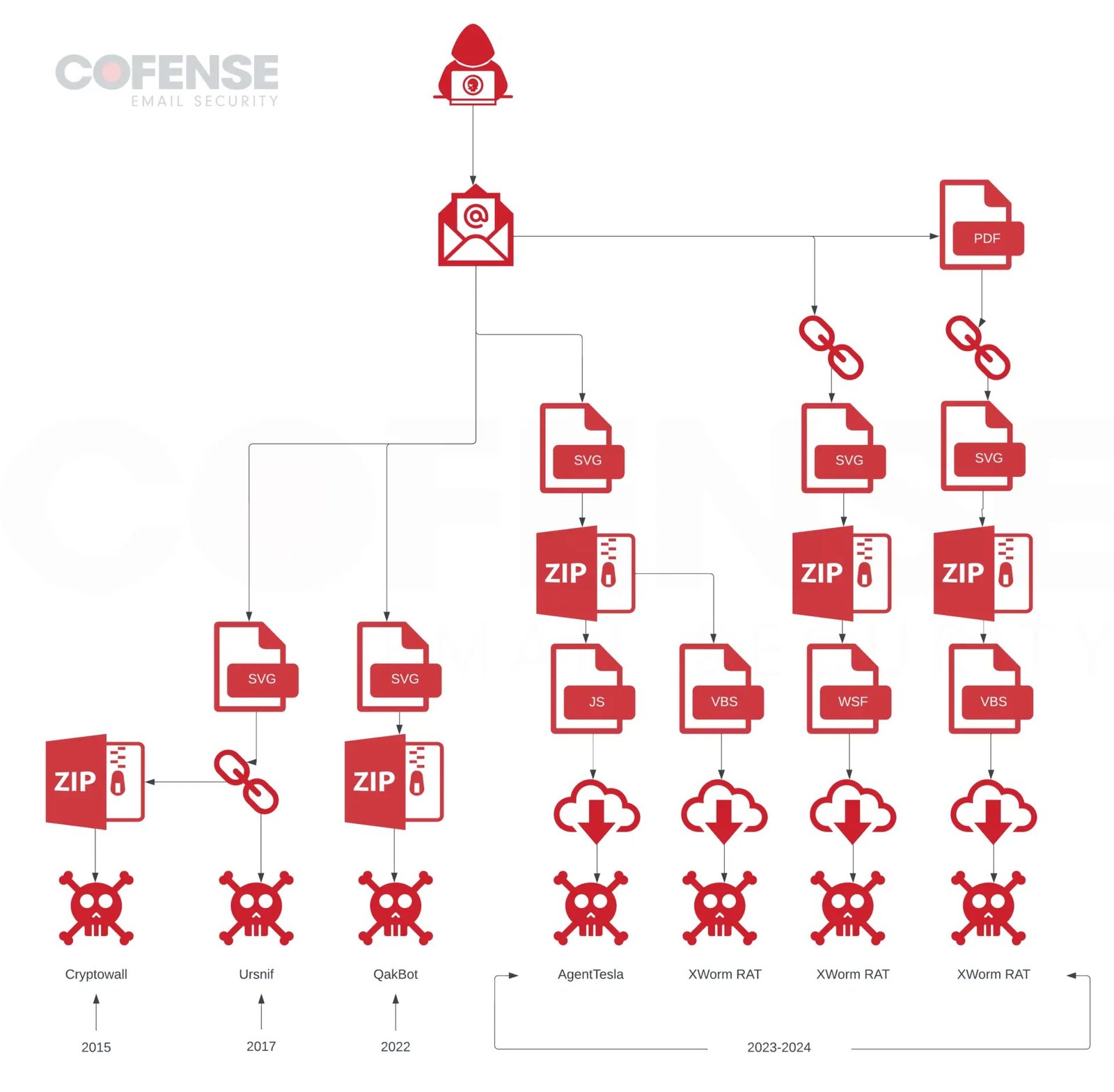
SVG files have been increasingly used for malware delivery since 2015 when they were first exploited to deliver ransomware by embedding malicious content. In 2017, SVG files downloaded Ursnif malware.
A major incident occurred in 2022 with SVG files containing embedded .zip archives that delivered QakBot malware via HTML smuggling, a new tactic different from previous external content downloads.
Recently, SVG files have been used to chain an exploit with smuggling capabilities to access Roundcube servers, as well as deliver Agent Tesla Keylogger and XWorm RAT in separate campaigns.
The versatility of SVG files across these varying tactics demonstrates their potential for malicious use.
AutoSmuggle, which debuted on GitHub in May 2022, covertly embeds executables or archives within SVG or HTML files, bypassing network defenses to deliver payloads.
This “smuggling” technique evades Secure Email Gateways (SEGs), unlike direct attachments.
Threat actors leverage this tactic to cloak malicious files as genuine HTML content, ensuring successful delivery upon victims opening the file.
Various methods exist for HTML/SVG file smuggling, with .zip archives within SVG files being prevalent in recent campaigns.
In the context of malware delivery, there are two major ways through which SVG files are used.
When an SVG file is opened in a browser, it usually leads to a download prompt irrespective of the method used.
At first, embedded URLs were exploited to deliver malware and later versions featured striking images as means of engaging users with downloaded payloads.
Both the 2015 and 2017 campaigns saw malicious content being externally sourced by SVG files instead of embedding it within themselves.
SVG files using smuggling techniques were later introduced, delivering embedded malicious files when opened.
They don’t display images; instead, they rely on the victim’s curiosity to engage with the delivered file.
Threat actors use SVG files because they’re treated with less suspicion than HTML or archives, making it easier to “smuggle” files inside them.
The campaigns utilizing SVG files to deliver Agent Tesla Keylogger and XWorm RAT had consistent infection chains involving attached SVG files that dropped embedded archives containing scripts to download and run the malware payloads.
Source: https://bit.ly/3uS5LZ2



