
Join the Certified Penetration Testing Professional (CPENT)
Unical Academy, in collaboration with EC-Council, invites you to enhance your cybersecurity skills with the Certified Penetration Testing Professional (CPENT) course. This globally recognized certification program includes comprehensive training and an exam voucher, giving you the expertise to protect systems from cyber threats.
Take the next step in your career and become a certified ethical hacker
About the course
Why Should You Join the Certified Penetration Testing Professional?
Gives a real-world experience through an Advanced Penetration Testing Range.
100% mapped with the NICE framework.
100% methodology-based penetration testing program.
Key Features

Advanced Windows Attacks

Privilege Escalation

Attacking IOT Systems
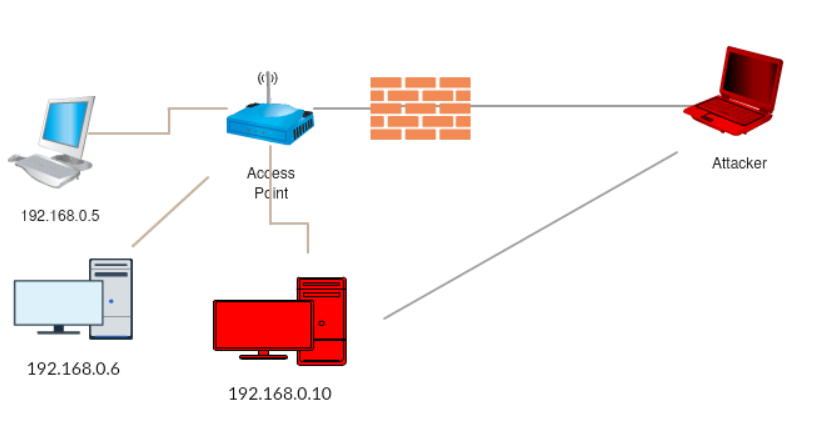
Double Pivoting

Writing Exploits: Advanced Binary Exploitation
Access Hidden Networks with Pivoting

Evading Defense Mechanisms

Bypassing a Filtered Network

Attack Automation with Scripts

Pentesting Operational Technology (OT)

Weaponize Your Exploits

Write Professional Reports
Enquire Now
The CPENT program is designed to help students master advanced penetration testing skills through real-world, dynamic cyber ranges that mimic live enterprise networks. The course offers hands-on experience in performing sophisticated attacks, bypassing security defenses, and exploiting vulnerabilities across various technologies, including IoT and OT systems.
Key learning objectives include:
- Advanced Windows Attacks: Learn to bypass security measures on Windows systems using PowerShell and other methods to gain unauthorized access.
- Attacking IoT Systems: Gain expertise in hacking IoT devices by locating, accessing, identifying firmware, extracting data, and performing reverse engineering.
- Advanced Binaries Exploitation: Identify and exploit flawed binaries through reverse engineering for privilege escalation.
- Bypassing a Filtered Network: Penetrate segmented architectures by analyzing filtering systems, compromising web applications, and extracting critical data.
- Pentesting Operational Technology (OT): Learn how to penetrate dedicated OT networks from the IT side, modify existing data, and understand critical infrastructure vulnerabilities.
- Access Hidden Networks with Pivoting: Break into direct networks by identifying filtering rules and performing single pivoting to access hidden networks.
- Double Pivoting: The first certification requiring testers to access hidden networks through manually configured double pivoting, a crucial skill for advanced testers.
- Attack Automation with Scripts: Master scripting languages like Perl, Python, Ruby, PowerShell, and BASH, as well as tools like Metasploit and fuzzing techniques to automate penetration testing.
- Weaponize Your Exploits: Learn to write custom code and create your own tools to exploit vulnerabilities and carry out penetration tests efficiently.
By the end of the program, students will be fully equipped to take on real-world penetration testing challenges, write their own exploits, automate attack processes, and tackle the CPENT certification exam with confidence.
- The exam can be given in 2 ways:
- 12-hour sessions
- single 24-hour exam
- Minimum passing percentage is 70%.
- And if you score 90%, then you get Licensed Penetration Tester (LPT) Designation
Who is it for?
- Ethical Hackers
- Application Security Analyst
- Penetration Testers
- Cybersecurity Assurance Engineer
- Network Server Administrators
- Security Operations Center (SOC) Analyst
- Firewall Administrators
- Technical Operations Network Engineer
- Security Testers
- Information Security Engineer
- System Administrators and Risk Assessment Professionals
- Network Security Penetration Tester
- Cybersecurity Forensic Analyst
- Network Security Engineer
- Cyberthreat Analyst
- Information Security Architect
- Cloud Security
- Analyst Information Security Consultant
Course Curriculum
Cover the fundamentals of penetration testing, including penetration testing approaches, strategies, methodologies, techniques, and various guidelines and recommendations for penetration testing.
Key topics covered:
Penetration Testing, Penetration Testing Service Delivery Models, ROI for Penetration Testing, Types of Penetration Assessment, Strategies of Penetration Testing, Selection of Appropriate Testing Type, Different Methods of Penetration Testing, Common Areas of Penetration Testing, Penetration Testing Process, Penetration Testing Phases, Penetration Testing Methodologies, EC-Council’s LPT Methodology, Qualities of a Licensed Penetration Tester, Characteristics of a Good Penetration Test, Ethics of a Penetration Tester; Qualification, Experience, Certifications, and Skills Required for a Pen Tester; Risks Associated with Penetration Testing
Learn the different stages and elements of scoping and engagement in penetration testing.
Key topics covered:
Penetration Testing: Pre-engagement Activities, Initiation of a Pen Testing Engagement Process, Proposal Submission, Determining the Project Schedule, Staffing Requirements, Rules of Engagement, Estimating the Timeline for the Engagement, Penetration Testing Schedule, Identifying the Reporting Time Scales, Deciding the Time of Day for the Test, ROE Document, Penetration Testing Contract, Penetration Testing “Rules of Behavior,” Confidentiality and Nondisclosure Agreement Clauses, Identifying the Security Tools Required for the Penetration Test, Preparing the Test Plan, Penetration Testing Hardware/Software Requirements, Gathering Information on the Client Organization’s History and Background, Identifying the Local Equipment Required for the Pen Test, Mission Briefing, Scope Creeping
Learn how to use techniques and tools to gather intelligence about the target from publicly available sources such as the World Wide Web (WWW), through website analysis, by using tools/frameworks/scripts, and so on.
Key topics covered:
OSINT through the WWW, OSINT through Website Analysis, OSINT through DNS Interrogation, Whois Lookups, Reverse Lookups, DNS Zone Transfer, Traceroute Analysis, Automating the OSINT Process using Tools/Frameworks/Scripts
This module covers the security configuration of network perimeter devices such as firewalls, intrusion detection and intrusion protection systems (IDSs/IPSs), routers, switches, etc., for effective perimeter protection.
Key topics covered:
Firewalls, firewall types, firewall topologies, firewall selection, firewall implementation and deployment, firewall administration, IDS/IPS, IDS/IPS classification, IDS/IPS selection, false positives, false negatives, router security, switch security, software-defined perimeter (SDP).
The hands-on lab exercises in this module help to demonstrate skills in perimeter security, which includes how to configure and implement firewalls and IDS/IPS with the help of well-known tools such as pfSense, Smoothwall, Windows Firewall, iptables, Suricata, Wazuh, ModSecurity, etc.
Learn how to implement a comprehensive penetration testing methodology for assessing networks from outsiders’ perspectives. Learn the process attackers follow to exploit the assets using vulnerabilities from the outside of the network perimeter.
Key topics covered:
Network Penetration Testing, External vs. Internal Penetration Testing, External Network Penetration Testing, Internal Network Penetration Testing. Network Penetration Testing Process, Port Scanning, Fingerprinting the OS, Examining the Patches Applied to the Target OS, fingerprinting the Services, External Vulnerability Assessment, searching and Mapping the Target with the Associated Security Vulnerabilities, Find Out the Security Vulnerability Exploits, Running the Exploits against Identified Vulnerabilities, Document the Result
Learn how to implement a comprehensive penetration testing methodology for assessing networks from insider’s perspectives.
Key topics covered:
Internal Network Penetration Testing, Footprinting, Network Scanning, Scanning Analysis, Scanning Methodology, OS and Service Fingerprinting, Identifying the OS, SMB OS Discovery, Manual Banner Grabbing, Identifying the Services, Displaying Services within Metasploit, Map the Internal Network, Enumeration, Vulnerability Assessment, Internal Vulnerability Assessment, Network Vulnerability Scanning, Host Vulnerability Scanner, Vulnerability Assessment Reports, Scan Analysis Process, Windows Exploitation, Unix/Linux Exploitation, Attempt Replay Attacks, Attempt ARP Poisoning, Attempt Mac Flooding, Conduct a Man-in-the-Middle Attack, Attempt DNS Poisoning, Automated Internal Network Penetration Testing, Post Exploitation, Pivoting, Port Forwarding, OS Discovery, Proxychains, Web Shells, Document the Result
Learn how to implement a comprehensive penetration testing methodology for assessing the security of network perimeter devices, such as Firewalls, IDS, Routers, and Switches.
Key topics covered:
Assessing Firewall Security Implementation, Testing the Firewall from Both Sides, Find Information about the Firewall, Enumerate Firewall Access Control List using Nmap, Scan the Firewall for Vulnerabilities, Trying to Bypass the Firewall Using Various Techniques, Assessing IDS Security Implementation, Common Techniques Used to Evade IDS Systems, Test for Resource Exhaustion, Test the IDS by Using Various Techniques, Assessing Security of Routers, Need for Router Testing, Identify the Router Operating System and its Version, Identify Protocols Running, Try to Gain Access to the Router, Test for IP Spoofing, Router Penetration Testing using Secure Cisco Auditor (SCA), Assessing Security of Switches, Test for Address of Cache Size, Test for Data Integrity and Error Checking, Test for Frame Error Filtering, Test for VLAN Hopping, Test for MAC Table Flooding, Testing for ARP Attack, Document the Result
Learn how to analyze web applications for various vulnerabilities, including the Open Web Application Security Project (OWASP) Top 10, and determine the risk of exploitation.
Key topics covered:
Web Application Penetration Testing, Web Application Security Frame, Security Frame vs. Vulnerabilities vs. Attacks, Website Footprinting, Web Enumeration, Discover Web Application Default Content, Discover Web Application Hidden Content, Conduct Web Vulnerability Scanning, Test for SQL Injection Vulnerabilities, Test for XSS Vulnerabilities, Test for Parameter Tampering, Test for Weak Cryptography Vulnerabilities, Tests for Security Misconfiguration Vulnerabilities, Test for Client-Side Attack, Tests for Broken Authentication and Authorization Vulnerabilities, Tests for Broken Session Management Vulnerabilities, Test for Web Services Security, Test for Business Logic Flaws, Test for Web Server Vulnerabilities, Test for Thick Clients Vulnerabilities.
Learn how to test various components of wireless networks, such as WLAN, RFID devices, and NFC technology devices.
Key topics covered:
Wireless Penetration Testing, Wireless Local Area Network (WLAN) Penetration Testing, Discovering the Wireless Networks, Detect Wireless Connections, Use a Wireless Honeypot to Discover Vulnerable Wireless Clients, Performing a Denial-of-Service Attack, Attempt Rapid Traffic Generation, Attempt Single-packet Decryption, Perform an ARP Poisoning Attack, Crack WPA-PSK Keys, Crack WPA/WPA2 Enterprise Mode, Check for MAC Filtering, Spoof the MAC Address, Create a Direct Connection to the Wireless Access Point, Introduction to RFID Penetration Testing, Perform Reverse Engineering, Perform Power Analysis Attack, Perform Eavesdropping, Perform an MITM Attack, Perform a DoS Attack, Perform RFID Cloning/Spoofing, Perform an RFID Replay Attack, Perform a Virus Attack; Oscilloscopes, RFID Antennas, and RFID Readers; Introduction to NFC Penetration Testing, Perform a Data Modification Attack, Perform Data Corruption Attack, Perform a MITM Attack, Document the Result
Understand various threats to Internet of things (IoT) networks and learn how to audit security controls for various inherent IoT risks.
Key topics covered:
IoT, Popular IoT Hacks, IoT Challenges, IoT Penetration Testing, Abstract IoT Testing Methodology, Attack Surface Mapping, IoT Architecture, Typical IoT Vulnerabilities, Steps to Analyzing the IoT Hardware, Firmware Attacks, Attack Surface Map, Sample Architecture Diagram, Sample Firmware Analysis Process, Binwalk to Extract the File System, Exploring the File System, Firmware Emulation
Understand OT and SCADA concepts and learn the process of testing various components of OT and SCADA networks
Key topics covered:
IT vs OT System Architecture, ICS/SCADA Protocols, Modbus, ICS and SCADA Pen Testing, Attack Monitoring, Testing Environment, Penetration Testing Actions, Host Attack Types, Network Attack Types, Ports of SCADA, Attack Modifications, OT Testing Tools, BACnet, Commercial SCADA Fuzzing Tool, Danger of Port Scanning, Types of Vulnerability Scans, Device Separation, ICS Cyber Test Impact
Understand various security threats and concerns in cloud computing and learn how to perform cloud penetration testing to determine the probability of exploitation.
Key topics covered:
Cloud Computing Security and Concerns, Security Risks Involved in Cloud Computing, Role of Penetration Testing in Cloud Computing, Scope of Cloud Pen Testing, Shared Responsibilities in Cloud; Penetration Testing Process, Identifying the Type of Cloud to be Tested, Identifying Tools for Penetration Testing, Perform Cloud Reconnaissance, Perform a Detailed Vulnerability Assessment, AWS Specific Penetration Testing, Attempt to Identify S3 Buckets, Azure Specific Penetration Testing, Google Cloud Platform Specific Penetration Testing, Google Cloud’s Provision for Penetration Testing
Understand the binary analysis methodology and reverse engineer applications to identify vulnerable applications that may lead to the exploitation of an information system.
Key topics covered:
Binary Coding, Machine Instructions, Sample Stack Frame, C program memory, Analyzing Binaries, Registers, Important IA-32 Instructions for Pen Testing, Executable and Linkable Format, Advanced Binary Analysis, Obfuscation Challenges, Binary Instrumentation, IA-64, Binary Analysis Methodology, Sample Program, Sample x86 C Program, Shellcode, ASLR, Return-to-libc vulnerability, Defeating the No-execute Stack, 64-bit Fundamentals, Attack using ROP.
This module covers threat, bandwidth, and performance monitoring with the help of network traffic monitoring and analysis.
Key topics covered:
Network traffic monitoring, baseline traffic signatures, suspicious network traffic signatures, threat detection with Wireshark, bandwidth monitoring, performance monitoring, network anomaly detection, and behavior analysis.
The hands-on lab exercises in this module help demonstrate skills in packet capturing, traffic monitoring, traffic analysis, threat detection, and bandwidth monitoring with tools such as Wireshark, tcpdump, PRTG, Capsa, NTOP, etc.
