Attackers exploit an unpatched Popup Builder vulnerability (CVE-2023-6000) to inject malicious code into vulnerable websites’ “Custom JS or CSS” sections. The code redirects users to phishing sites or injects further malware, and the campaign has already infected over 3300 websites. …
COM (Component Object Model) hijacking is a technique in which threat actors exploit the core architecture of Windows by adding a new value on a specific registry key related to the COM object. This allows the threat actors to achieve …
Threat actors use weaponized PDF files to exploit software vulnerabilities, enabling them to execute malicious code on a target system.
The upsurge of Apple products has made Mac users the prime targets for hackers who use malware to exploit them.
Concerning a development for internet security, a new form of website malware known as “Angel Drainer” has been increasingly targeting Web3 and cryptocurrency assets since January 2024.
When it comes to access security, one recommendation stands out above the rest: multi-factor authentication (MFA). With passwords alone being simple work for hackers, MFA provides an essential layer of protection against breaches.
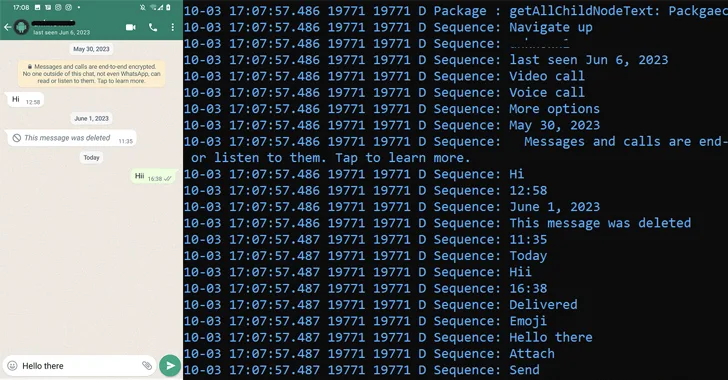
The threat actor known as Patchwork likely used romance scam lures to trap victims in Pakistan and India, and infect their Android devices with a remote access trojan called VajraSpy.
Persistence is one of the key things for threat actors to maintain their access to compromised systems and establish connections whenever they require.
Threat actors operating with interests aligned to Belarus and Russia have been linked to a new cyber espionage campaign that likely exploited cross-site scripting (XSS) vulnerabilities in Roundcube webmail servers to target over 80 organizations.
A critical security flaw in the Bricks theme for WordPress is being actively exploited by threat actors to run arbitrary PHP code on susceptible installations.