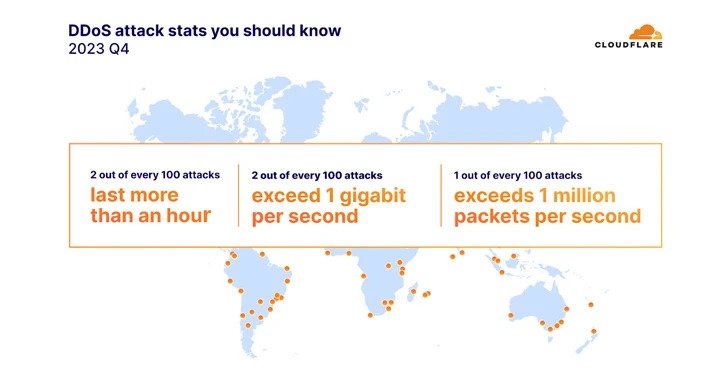
The environmental services industry witnessed an “unprecedented surge” in HTTP-based distributed denial-of-service (DDoS) attacks, accounting for half of all its HTTP traffic.
This Maldives cyberattack incident occurred amidst a broader context of diplomatic tensions.
Banmali Agrawala of Tata Advanced Systems (TASL) on Monday said the notion that one can ‘leapfrog’ into design without understanding manufacturing reflects an improper understanding of the manufacturing process.
Developing and maintaining robust cybersecurity policies and procedures is a crucial aspect of a CISO’s role. These policies must address various aspects of security, including data protection, access controls, incident response, and compliance with industry and regulatory standards, says Lt. General Rajesh Pant.
Sharp spike in cybercrimes, dip in crimes against women in Cyberabad police limits
Researchers have uncovered a flaw that lets hackers access people’s Google accounts without needing their passwords.
Cybersecurity, short for “cybersecurity,” refers to the practice of protecting computer systems, networks, and digital information from theft, damage, unauthorized access, or any form of cyber threats. It encompasses a broad range of measures and technologies designed to safeguard the …
The field of cybersecurity offers a diverse range of career opportunities, and the demand for skilled professionals continues to grow as organizations recognize the importance of securing their digital assets. Here are some common careers in cybersecurity: 1. Security Analyst: …
Investing in cybersecurity is generally considered worthwhile for several reasons: 1. Protecting Assets: Cybersecurity measures help protect sensitive data, intellectual property, financial information, and other valuable assets. The potential losses resulting from a cyber-attack can far outweigh the initial investment …
In today’s digitally interconnected landscape, the necessity of conducting regular security audits for every website cannot be overstated. A security audit serves as a proactive and comprehensive examination of a website’s infrastructure, code, and overall cybersecurity measures. Here are compelling …