Cybersecurity researchers have discovered a new Java-based “sophisticated” information stealer that uses a Discord bot to exfiltrate sensitive data from compromised hosts.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday issued an emergency directive urging Federal Civilian Executive Branch (FCEB) agencies to implement mitigations against two actively exploited zero-day flaws in Ivanti Connect Secure (ICS) and Ivanti Policy Secure (IPS) products.
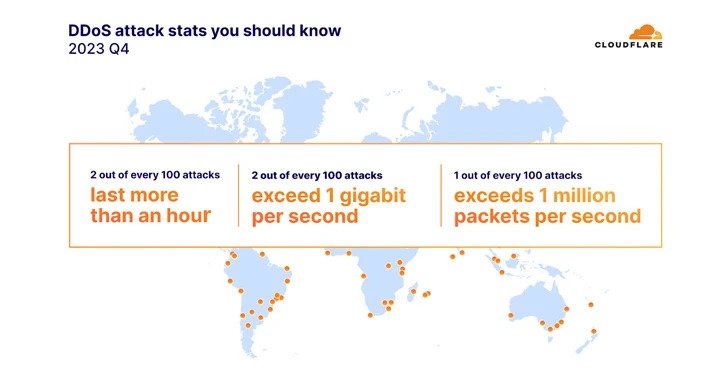
The environmental services industry witnessed an “unprecedented surge” in HTTP-based distributed denial-of-service (DDoS) attacks, accounting for half of all its HTTP traffic.
This Maldives cyberattack incident occurred amidst a broader context of diplomatic tensions.
Banmali Agrawala of Tata Advanced Systems (TASL) on Monday said the notion that one can ‘leapfrog’ into design without understanding manufacturing reflects an improper understanding of the manufacturing process.
Chris Wood, the esteemed Vice President and General Manager of Quest, sheds light on the strategies and solutions that Quest offers to help organizations successfully navigate their digital journeys
Sharp spike in cybercrimes, dip in crimes against women in Cyberabad police limits
Researchers have uncovered a flaw that lets hackers access people’s Google accounts without needing their passwords.
Developing and maintaining robust cybersecurity policies and procedures is a crucial aspect of a CISO’s role. These policies must address various aspects of security, including data protection, access controls, incident response, and compliance with industry and regulatory standards, says Lt. General Rajesh Pant.
OpenAI promises enterprise-grade security along with a host other features