Hackers often abuse weaponized Word docs, as they can contain macros that contain or exploit flaws inside those Word files to run destructive code upon being opened by the intended victims. It enables an attacker to employ this tool to …
A newly discovered security vulnerability allows attackers to impersonate Microsoft corporate email accounts, significantly increasing the risk of phishing attacks. Security researcher Vsevolod Kokorin, also known as Slonser, found this bug, which Microsoft has not yet patched. Kokorin revealed the …
Researchers analyzed real-world passwords leaked on the dark web instead of artificial ones used in labs, as their findings showed that a worrying 59% of these passwords could be cracked within an hour using just a modern graphics card and …
Fortinet, a global leader in broad, integrated, and automated cybersecurity solutions, has announced its acquisition of Lacework, an AI-powered cloud-native application protection platform (CNAPP). This strategic move aims to enhance Fortinet’s already comprehensive cybersecurity platform by integrating Lacework’s advanced cloud …
RedSecLabs security researchers Rafay Baloch and Muhammad Samaak have uncovered address bar spoofing vulnerabilities in widely used mobile browsers such as Safari, Microsoft Edge, and DuckDuckGo. These vulnerabilities have a significant impact, affecting millions of users worldwide. The Severity of Address Bar …
Google Chrome recently implemented Shared Memory Versioning, improving its speed through more effective cookie handling. This upgrade improves Chrome and other Chromium-powered browsers like Microsoft Edge and Vivaldi. Resource contention arises as more people rely on the Internet to do their daily …
A new vulnerability has been discovered in Ariane Allegro Scenario Player in a Kiosk mode that could allow threat actors to bypass the Kiosk mode and access the underlying Windows Desktop. The CVE for this vulnerability is yet to be …
Hackers use JavaScript frameworks since they offer a wide range of functionalities and tools that could be used to bypass detection, hide code, and carry out harmful acts. In addition, they take advantage of the people’s trust in such popular …
Cybersecurity experts have identified a critical zero-day vulnerability in Checkpoint’s security software that hackers are actively exploiting. The flaw assigned to the identifier CVE-2024-24919 poses a significant threat to organizations relying on Checkpoint’s solutions for their cybersecurity needs. Details of …
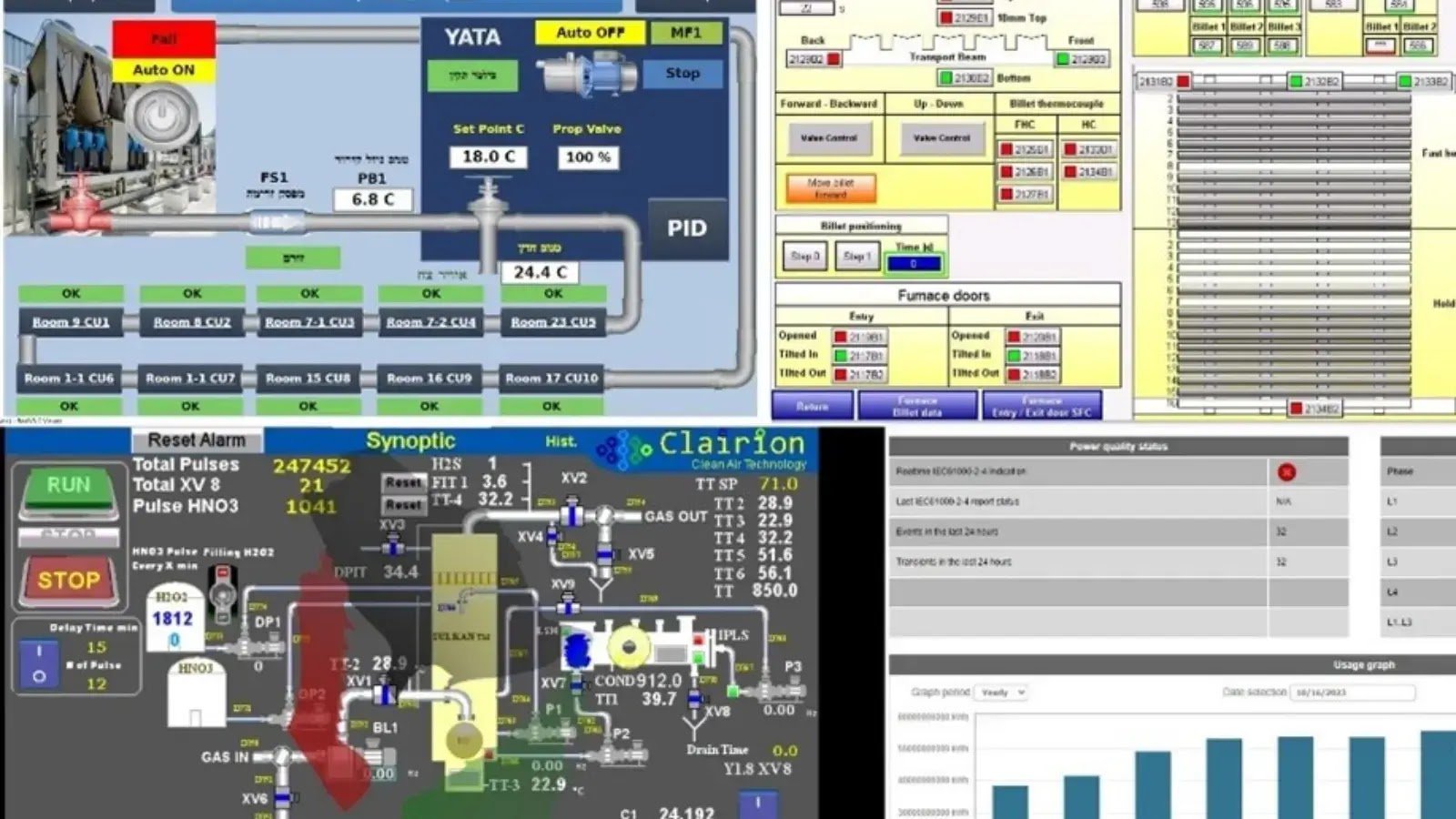
Microsoft has reported a significant increase in cyberattacks targeting internet-exposed, poorly secured operational technology (OT) devices. These attacks have particularly focused on the United States’ water and wastewater systems (WWS). Various nation-backed actors, including the IRGC-affiliated “CyberAv3ngers” and pro-Russian hacktivists, …