It has been found that almost one-fifth of the repositories on Docker Hub, a popular platform for developers to store and share containerized applications, have been exploited to spread malicious software and phishing scams. This is a concerning discovery for …
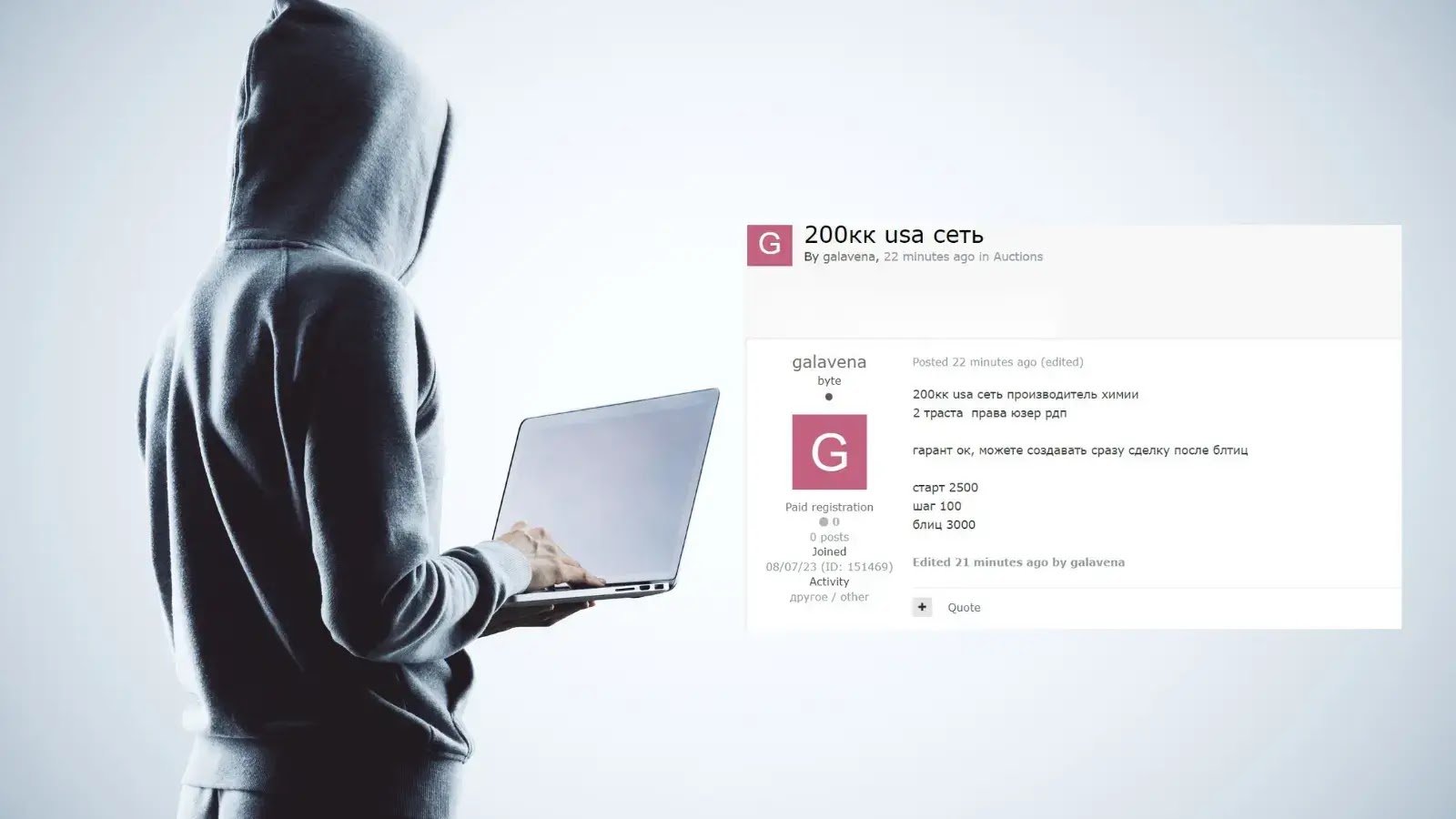
Cybersecurity communities are on high alert as threat actors have begun selling Remote Desktop Protocol (RDO) access on underground hacker forums. This alarming trend poses significant risks to individual and organizational cybersecurity, potentially allowing unauthorized access to sensitive information and critical systems. …
Operation PANDORA has successfully dismantled a network of 12 fraudulent call centers, dealing a significant blow to a sophisticated criminal enterprise that has stolen over €10 million from unsuspecting victims. This landmark operation, spearheaded by Europol, marks a critical step forward …
McAfee has introduced a significant upgrade to its AI-powered deepfake detection technology. This enhancement, developed in collaboration with Intel, aims to provide a robust defense against the escalating threat of deepfake scams and misinformation. The McAfee Deepfake Detector utilizes the advanced capabilities …
Ukrainian hackers have successfully infiltrated and disabled a vast network of industrial sensors and monitoring infrastructure in Russia, leading to a significant shutdown of sewage systems, among other utilities. The group, known as BlackJack, executed the attack on the 9th of April, …
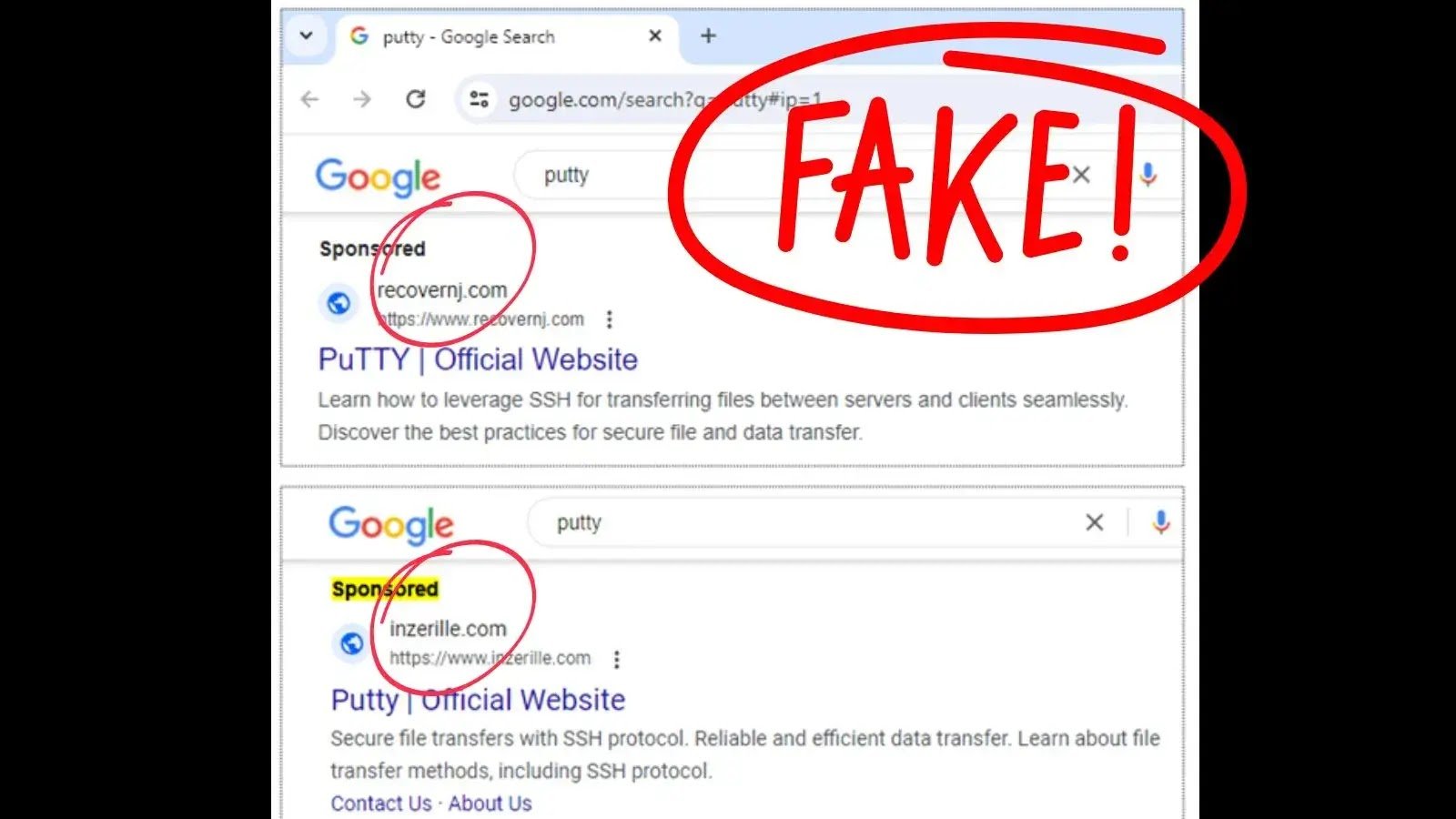
A sophisticated malvertising campaign is targeting system administrators across North America. The attackers are using fake ads for popular system utilities to distribute a dangerous strain of malware known as Nitrogen. Step 1: Luring Victims with Malicious Ads The campaign exploits the trust users place in search engine advertisements. By displaying sponsored search results for …
Node.js project disclosed a high-severity vulnerability affecting multiple active release lines of its software on Windows platforms. This flaw, identified as CVE-2024-27980, allows attackers to execute arbitrary commands on affected systems, posing a serious risk to applications and services built …
Over a million WordPress websites have been at risk due to a critical SQL Injection vulnerability discovered in the popular LayerSlider plugin. The flaw, CVE-2024-2879, could allow unauthenticated attackers to extract sensitive data, including password hashes, from websites’ databases. CVE-2024-2879: A Critical …
Apache released updates to address several vulnerabilities impacting the Apache HTTP server that let attackers launch HTTP/2 DoS attacks and insert malicious headers. Server operations are being adversely affected by these vulnerabilities, which are proving to be a serious danger. A …
Hospitals across the nation are on high alert as sophisticated cybercriminals use advanced social engineering tactics to target IT help desks. The Health Sector Cybersecurity Coordination Center (HC3) has issued a Sector Alert detailing the latest threat to the healthcare industry. The HC3’s …