The Russia-linked threat actor known as COLDRIVER has been observed evolving its tradecraft to go beyond credential harvesting to deliver its first-ever custom malware written in the Rust programming language.
New assessment focuses on how AI will impact the efficacy of cyber operations and the implications for the cyber threat over the next two years.
Remote desktop software maker AnyDesk disclosed on Friday that it suffered a cyber attack that led to a compromise of its production systems.
In 2024, an era where organisations and individuals increasingly operate online, the landscape of cybercrime is evolving rapidly. India, a burgeoning hub for fintech, has experienced a significant surge in cybercrime
A large-scale cyber attack was launched to steal and market confidential user information, focusing mainly on the APAC region’s employment agencies and retail firms.
What is the difference between Vulnerability Assessment and Penetration Testing?Vulnerability Assessment focuses on identifying and classifying vulnerabilities in a system, while Penetration Testing involves actively exploiting vulnerabilities to assess the real-world impact. How often should VAPT be conducted?The frequency of …
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday issued an emergency directive urging Federal Civilian Executive Branch (FCEB) agencies to implement mitigations against two actively exploited zero-day flaws in Ivanti Connect Secure (ICS) and Ivanti Policy Secure (IPS) products.
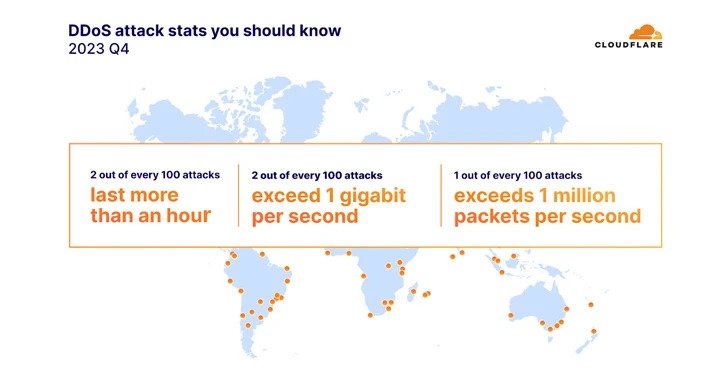
The environmental services industry witnessed an “unprecedented surge” in HTTP-based distributed denial-of-service (DDoS) attacks, accounting for half of all its HTTP traffic.
Greece bolsters its digital defenses with the establishment of the National Cybersecurity Authority, a pivotal step in safeguarding against hackers and ransomware threats across public and private sectors.
Amidst the dynamic shifts within the cybersecurity world, where each digital step forward unveils new challenges, organizations face a relentless pursuit to secure their virtual domains