Hackers Attacking Infra Teams With Fake PuTTY & FileZilla Ads
A sophisticated malvertising campaign is targeting system administrators across North America.
The attackers are using fake ads for popular system utilities to distribute a dangerous strain of malware known as Nitrogen.
Step 1: Luring Victims with Malicious Ads
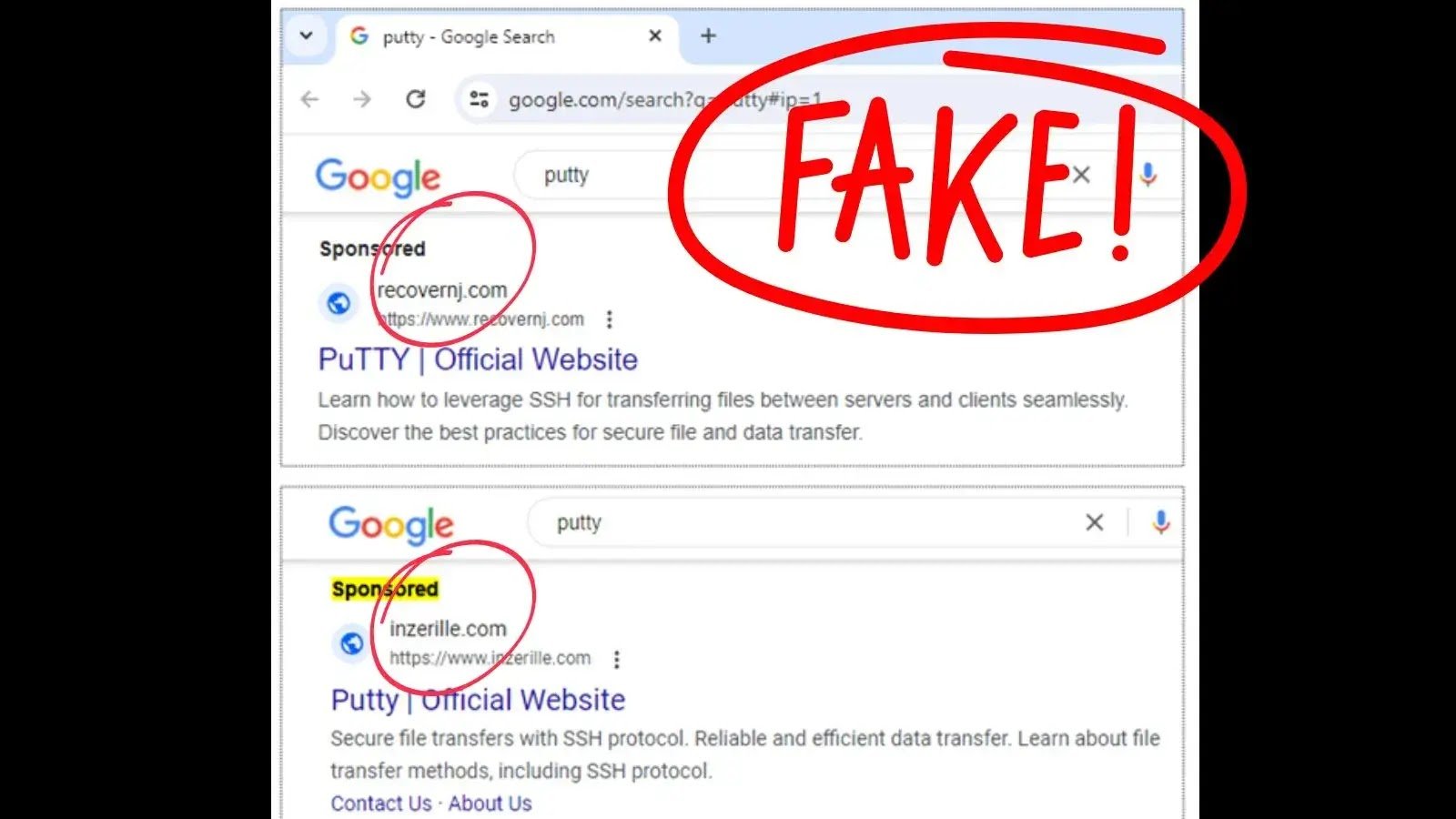
The campaign exploits the trust users place in search engine advertisements. By displaying sponsored search results for utilities like PuTTY and FileZilla, the attackers can lure in their victims.
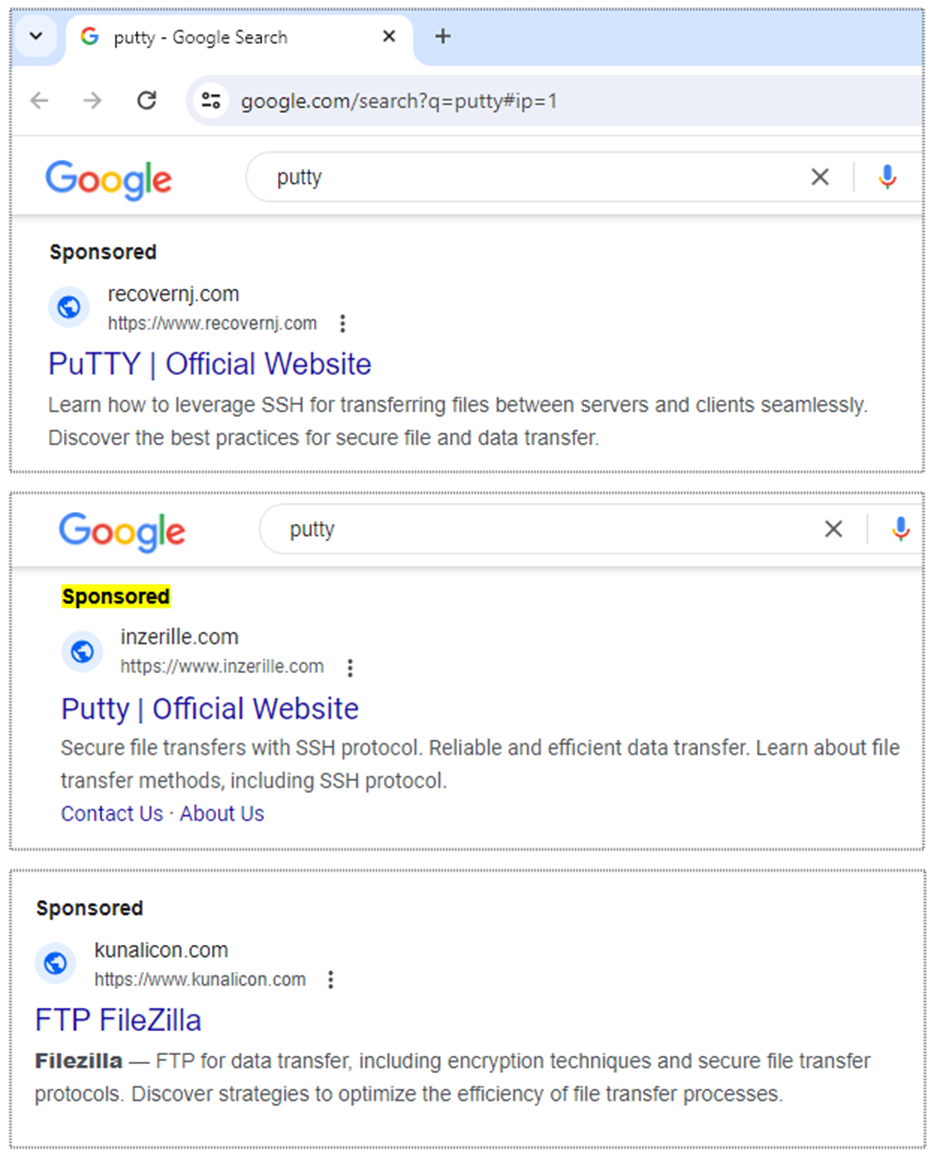
These ads are convincing and tailored to the search habits of IT professionals, making them particularly effective.
Once clicked, these malicious ads lead users to download what they believe to be legitimate software installers.
However, these installers are trojanized versions designed to infect the user’s system with Nitrogen malware.
This malware serves as a gateway for attackers to gain initial access to private networks, which can then be exploited for data theft or to deploy ransomware such as BlackCat/ALPHV.
Despite reports to Google, the malicious ads continue to run, prompting the cybersecurity community to share detailed information on the tactics, techniques, and procedures (TTPs) used by the attackers and indicators of compromise (IOCs) to help system administrators defend against these threats.
A recent article published in Malwarebytes Labs highlighted that hackers are now targeting infrastructure teams using fake ads for PuTTY and FileZilla.
Step 2: Deception Through Lookalike Sites
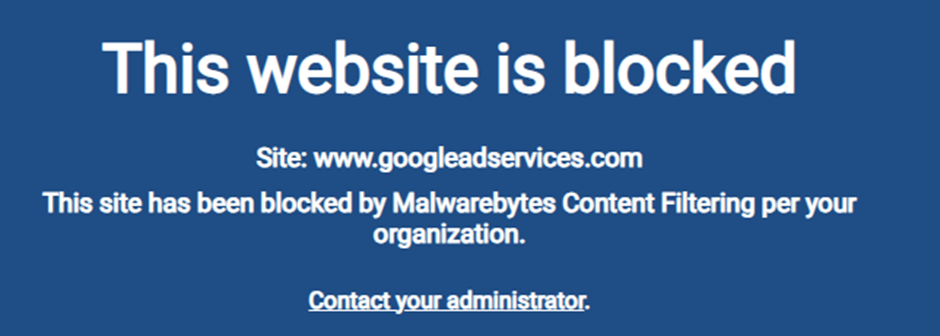
The attackers have set up a sophisticated malvertising infrastructure that uses cloaking techniques to evade detection.
Depending on the situation, users who click on the ads may be redirected to a harmless decoy site or a video of Rick Astley—a tactic used to mock security researchers.
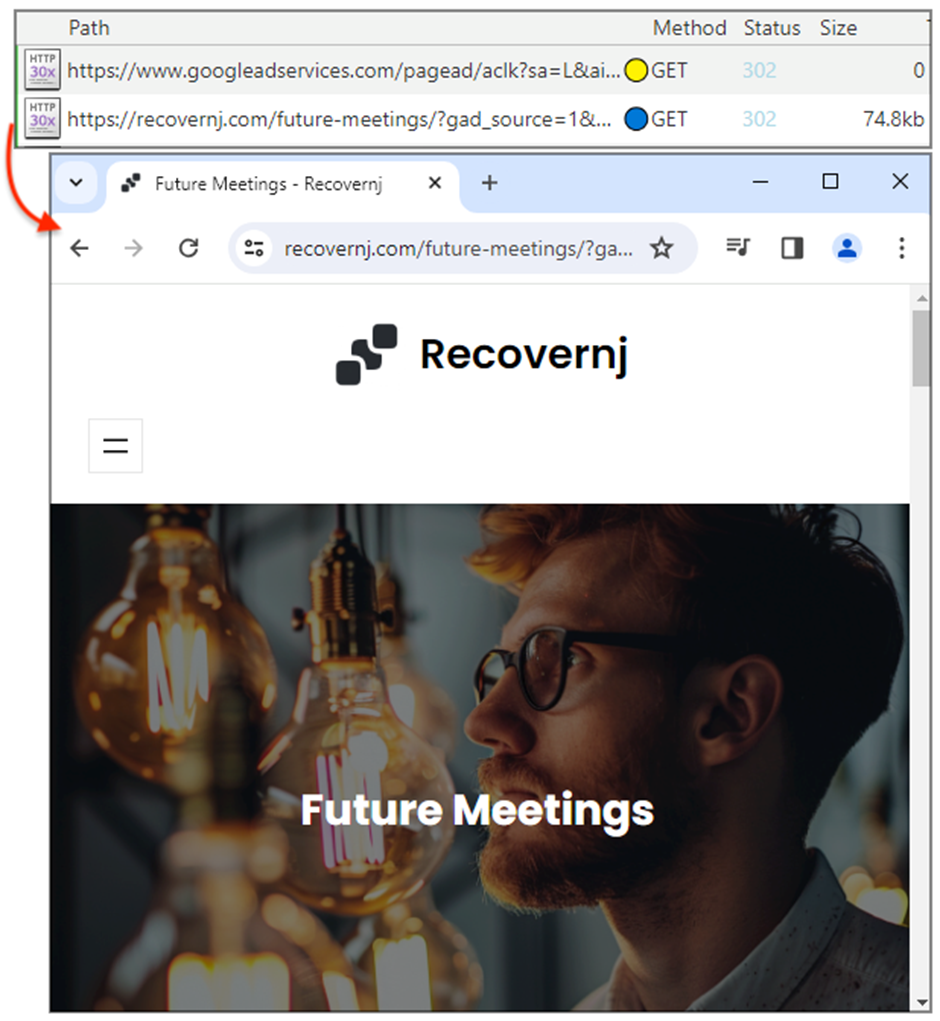
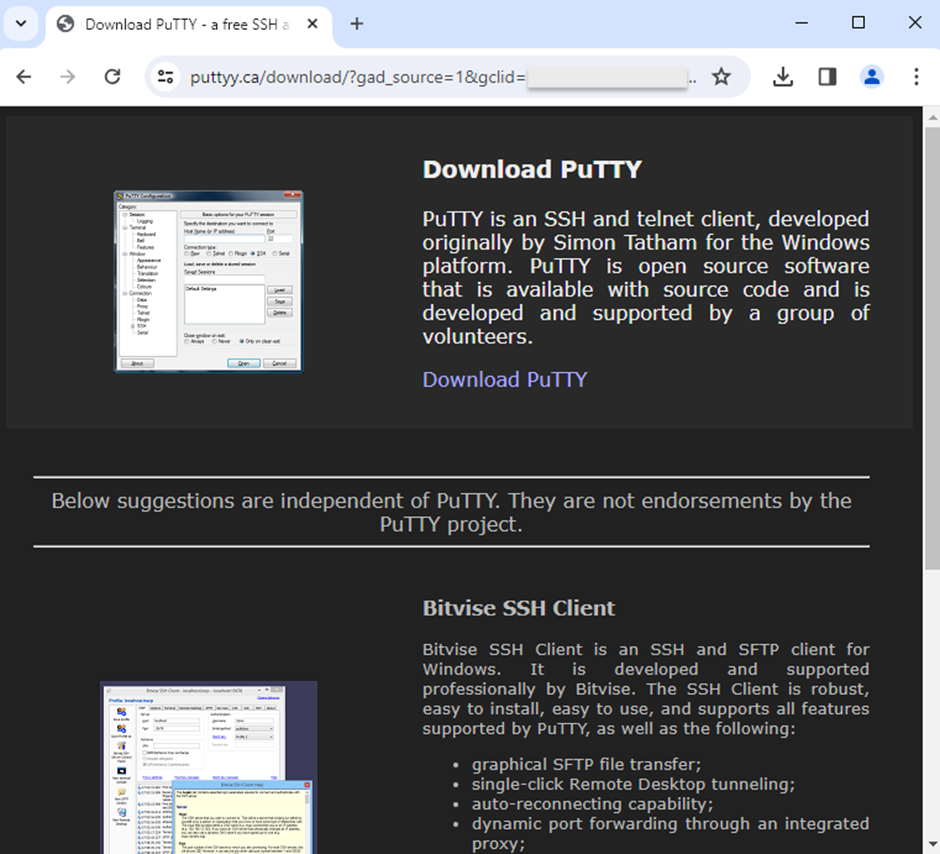
However, for potential victims, the redirect leads to lookalike sites convincing replicas of the legitimate software pages they are impersonating.
These sites are designed to be as deceptive as possible, increasing the likelihood that someone will download the malware-laden installers.
Step 3: Deploying Malware and Protecting Against Attacks
The final step in this malicious chain is deploying the Nitrogen malware through the fraudulent installers.
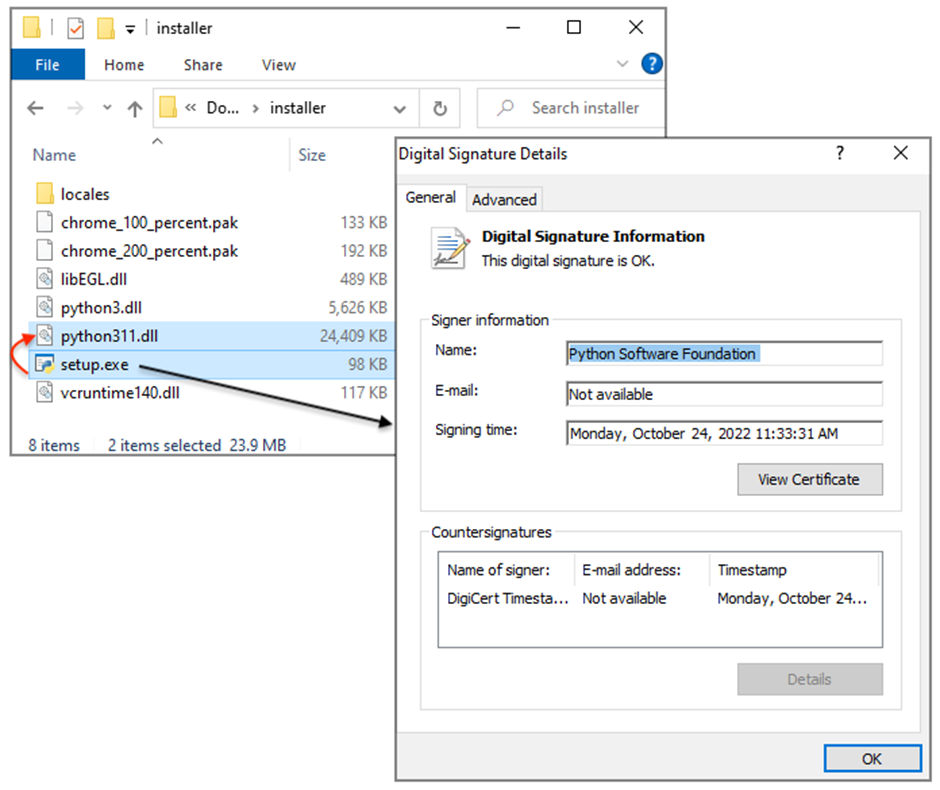
The malware uses a technique known as DLL sideloading, where a legitimate executable is used to launch a malicious DLL file.
In this instance, a seemingly innocuous setup.exe file sideloads a dangerous file named python311.dll, which is associated with Nitrogen.
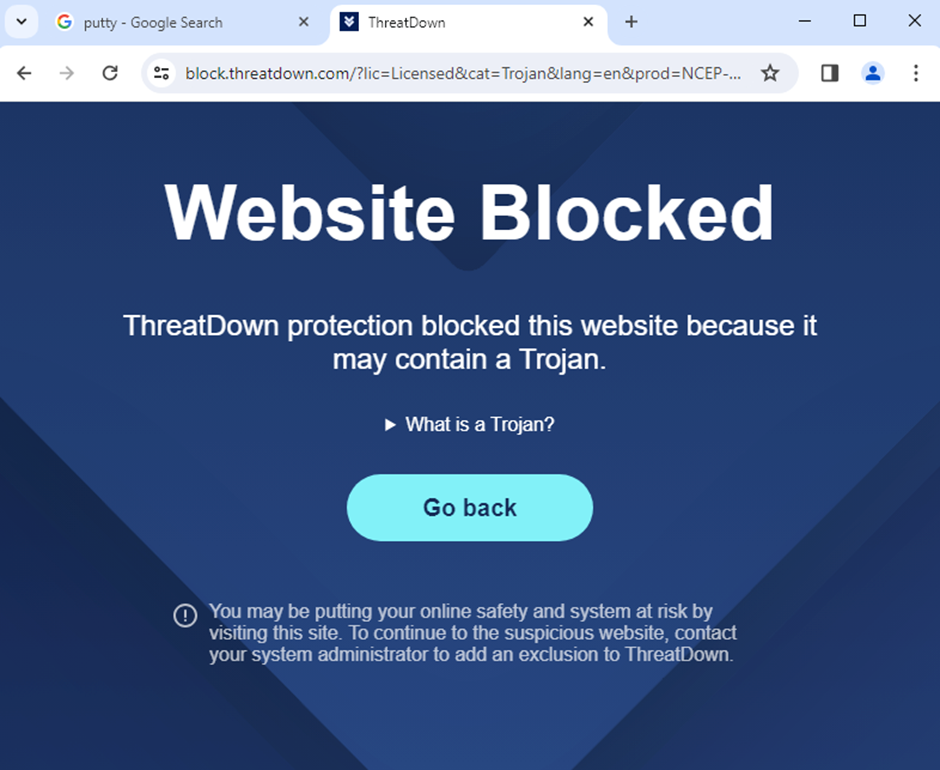
To combat this threat, cybersecurity firm ThreatDown has blocked these malicious websites and prevented users from being tricked into downloading malware.
Their Endpoint Detection and Response (EDR) engine can quarantine the malicious DLL immediately, and system administrators can use the AI-assisted engine to search for and review detections.
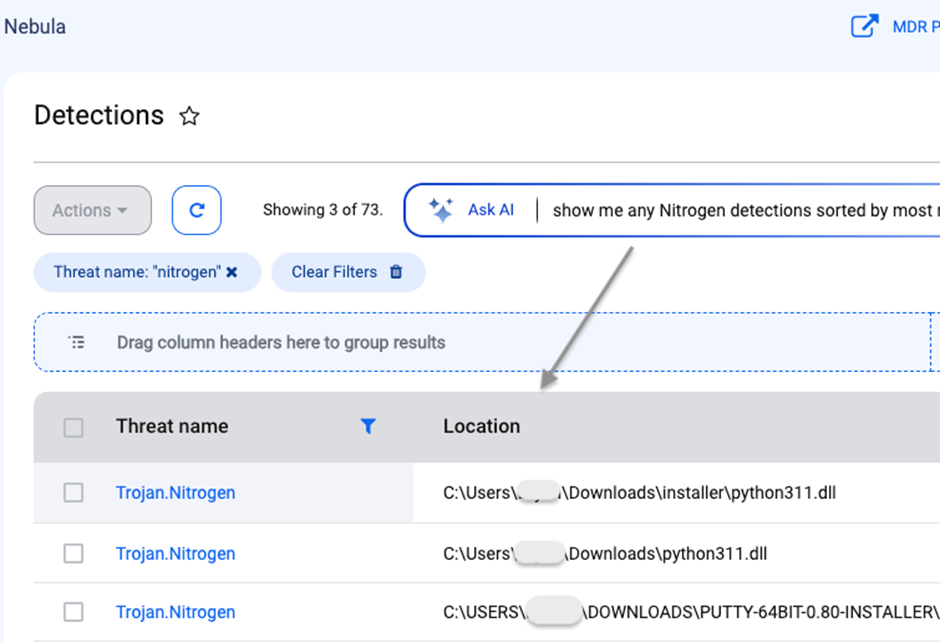
System administrators can log into their console and use the AI-assisted engine
Source: https://bit.ly/3uS5LZ2



