OWASP Top 10: 2025
- Posted by Sharath Kumar
- Categories Articles, News
- Date January 17, 2026
What It Means for Modern Web Application Security
In an era where web applications form the backbone of digital business, application security is no longer optional—it is foundational. The release of the OWASP Top 10: 2025 – Revised Edition marks a significant milestone in how the global security community understands, prioritizes, and mitigates modern web application risks. For organizations, developers, security professionals, and aspiring cybersecurity practitioners, this update is more than just a list—it is a strategic roadmap to building secure, resilient, and trustworthy applications. At Unical Academy, where we focus on industry-aligned cybersecurity training and hands-on skill development, understanding such global standards is at the core of our teaching philosophy.
Understanding the OWASP Top 10
The OWASP (Open Worldwide Application Security Project) Top 10 is a globally recognized awareness document that represents the most critical security risks to web applications. It is based on real-world vulnerability data, expert analysis, and industry trends.
Security teams, auditors, developers, and compliance frameworks worldwide rely on the OWASP Top 10 to:
- Guide secure application design
- Prioritize vulnerability remediation
- Shape secure coding standards
- Align security testing and VAPT methodologies
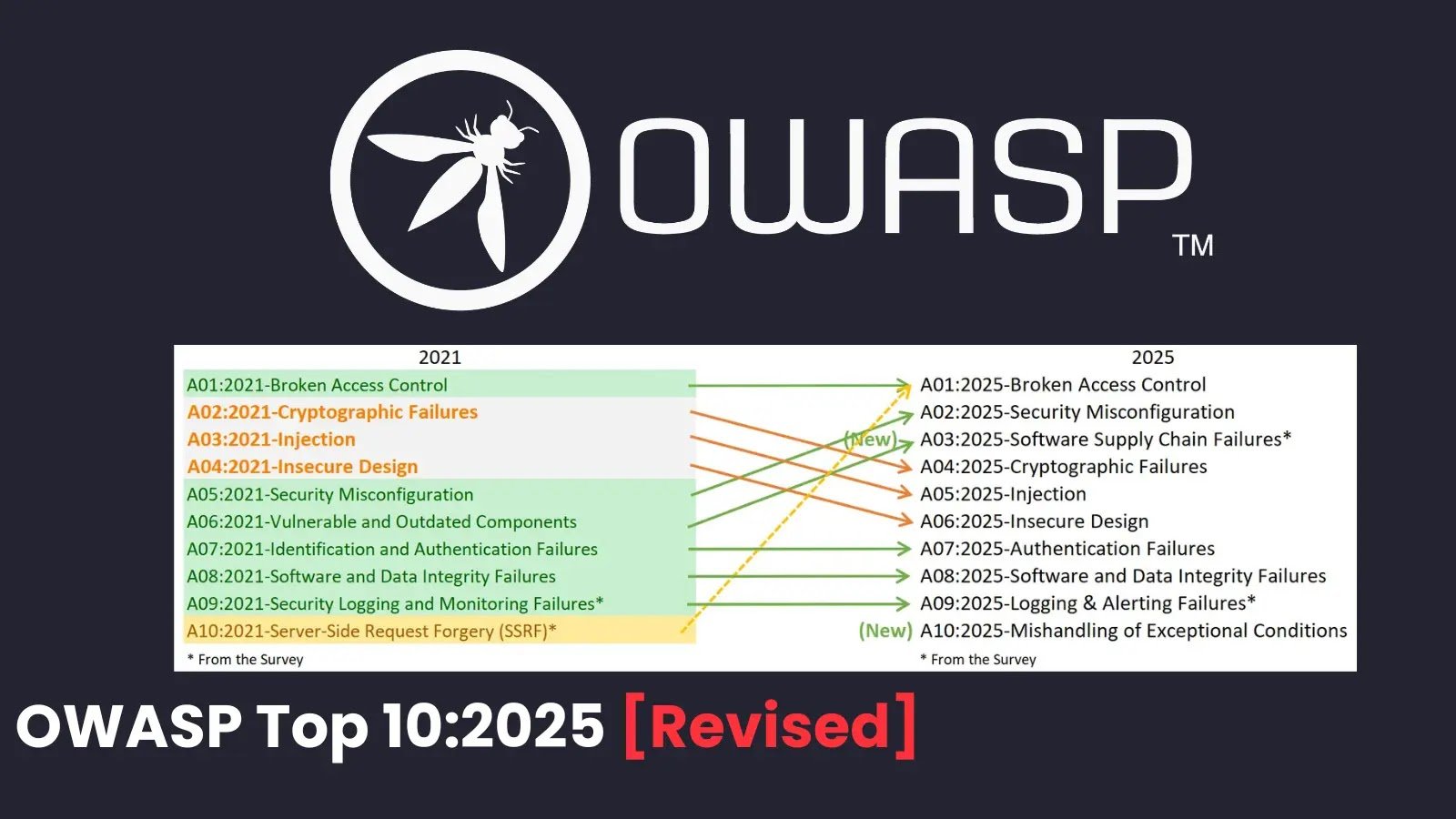
The 2025 revised edition reflects the rapidly evolving threat landscape driven by cloud adoption, APIs, CI/CD pipelines, and third-party dependencies.
Two New Risk Categories Introduced
1. Software Supply Chain Failures
Modern applications are no longer built from scratch. They rely heavily on:
- Open-source libraries
- Third-party APIs
- Cloud services and SDKs
- CI/CD tools and plugins
A vulnerability in any external dependency can compromise the entire application.
This category highlights risks such as:
- Compromised or malicious libraries
- Dependency confusion attacks
- Insecure package updates
- Weak integrity validation in build pipelines
The inclusion of this category reflects real-world incidents where trusted software components became attack vectors.
2. Mishandling of Exceptional Conditions
Error handling is often overlooked—but attackers actively exploit it.
This risk focuses on:
- Verbose error messages
- Stack trace exposure
- Improper exception handling
- Application crashes leading to denial of service or information leakage
Poorly handled exceptions can reveal:
- Application logic
- Database structures
- File paths
- Security controls
Robust error handling is now recognized as a security requirement, not just a development best practice.
Key Structural Changes in the 2025 Update
Security Misconfiguration Now Ranks #2
Security Misconfiguration has risen in priority due to its prevalence in:
- Cloud environments
- Containerized applications
- Default credentials and settings
- Over-permissive access controls
Misconfigurations remain one of the easiest vulnerabilities to exploit and one of the hardest to consistently eliminate without strong processes and automation.
SSRF Merged Under Broken Access Control
Server-Side Request Forgery (SSRF) is no longer a standalone category. It is now grouped under Broken Access Control, emphasizing that SSRF is fundamentally an authorization and trust boundary failure.
This change encourages security teams to address root causes rather than treating SSRF as an isolated issue.
Greater Emphasis on Software Integrity & Secure Development
The 2025 OWASP Top 10 places stronger focus on:
- Secure CI/CD pipelines
- Code signing and integrity checks
- Dependency monitoring
- Secure configuration management
- Shift-left security practices
This aligns with the industry’s move toward DevSecOps, where security is embedded throughout the development lifecycle.
Why the OWASP Top 10: 2025 Matters for Students & Professionals
For cybersecurity learners, this update defines what employers expect in real-world roles.
For developers, it highlights where secure coding efforts must evolve.
For security professionals, it reshapes how:
- Web Application VAPT is performed
- Risk is reported to management
- Security controls are prioritized
Understanding OWASP Top 10 is also essential for certifications such as:
- CEH (Certified Ethical Hacker)
- Web Application Security Testing roles
- SOC and AppSec careers
How Unical Academy Aligns with OWASP 2025
At Unical Academy, we continuously update our:
- Training curriculum
- Hands-on labs
- Real-world attack simulations
- Vulnerability assessment methodologies
Our approach ensures learners gain:
- Practical understanding of OWASP Top 10 risks
- Hands-on experience exploiting and mitigating vulnerabilities
- Industry-ready skills aligned with global standards
We emphasize:
- Concept → Demonstration → Hands-on Labs
- Real-world attack scenarios
- Secure coding and defensive strategies
This ensures our students are not just certified—but job-ready.
Final Thoughts
The OWASP Top 10: 2025 (Revised) is a clear signal that application security is evolving beyond traditional vulnerabilities. Supply chain risks, configuration weaknesses, and secure error handling are now front-line concerns.
Organizations that proactively adapt will be better protected. Professionals who stay updated will remain relevant. Students who learn these standards early will gain a competitive edge.
At Unical Academy, we believe that staying informed is the first step to staying secure.
Stay informed. Stay secure.
For training, workshops, and web application security programs aligned with OWASP and global standards, connect with Unical Academy.
Source: https://owasp.org/Top10/2025/0x00_2025-Introduction/



